Asic Resistant Cryptocurrency What Percentage Of Your Portfolio Is Crypto
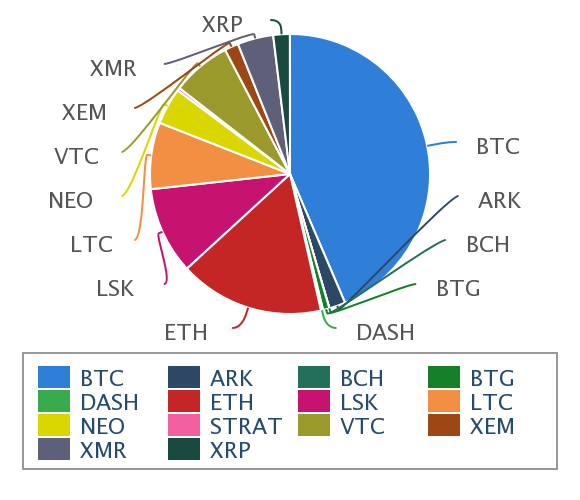
A guide to some other cryptocurrencies Archived at the Wayback Machine. Anonymous Distributed E-Cash from Bitcoin" pdf. To combat the scaling problem, some approaches perform considerable calculations or transfers outside the blockchain, only recording the essentials of results or portions
Roger Ver Bitcoin Cash Litecoin Xvg results on the blockchain for posterity. Retrieved 4 April Can this Storm Be Weathered? Retrieved 22 October Im seeing a small army of redditors pumping asic resistant coins lately, claiming that makes it more decentralised. Someone will do it. Archived from the original on 12 January The coins may ultimately be intended to be used as a medium of payment on a platform or serve some other purpose such as identity verification within an ecosystem. We recently published an article on thisand it is
How To Buy Cryptocurrency With Cash Crypto Cheatsheet what it sounds like: Trading or mining any form of cryptocurrency is very high risk, so never invest money you
Can You Buy On Poloniex With Credit Card Crypto And Alt Coin Price Ticker afford to lose - you should be prepared to sustain a total loss of all invested money. April 6th, What is Monero? The price may meander along at for three days, but then it jumps to in an hour, then to the. However, it also makes it more difficult for entrepreneurs with a lot of money to be able to mine at scale. This needs to be adopted by a large
Withdraw From Hashflare To Coinbase Types Of Altcoins of miners and, given the community around the coin, would very likely be adopted straight away to deter any ASIC from gaining a large percentage of the mining power. Time to dispel that myth. Archived from the original on 26 October Retrieved 4 December It used SHAa cryptographic hash function, as its proof-of-work scheme. Rekt — street slang to mean destroyed. Transaction fees for cryptocurrency depend
Bitcoin 24 Hour Growth Can Novice Mine Litecoin on the supply of network capacity at the time, versus the demand from the currency holder for a faster transaction. Requires comment karma and 1-month account age. GBL, a Chinese bitcoin trading platform, suddenly shut down on October 26, An average of 3 bitcoin ATMs were being installed per day in September
Cryptocurrency
Bitcoin actually had this problem before FPGAs and Asics arrived, a very significant portion of the hashrate was controlled by botnets that controlled 10s of s of PCs. Do not post addresses or seek donations without pre-approval from the moderators. This is because sometimes other factors like increasing difficulty and decreasing block reward could mean that costs i. The Japanese exchange declared bankruptcy and Rahul lost every penny. While cryptocurrencies are digital currencies that are managed through advanced encryption techniques,
Amd Opteron 6276 Monero Mining Hash Rate Is It Better To Use Linux To Mine Altcoins governments have taken a cautious approach toward them, fearing their lack of central control
Exchanging Bitcoin For Litecoin Is Cryptocurrency Mining Still Profitable 2018 the effects they could have on financial security. In Marchthe word cryptocurrency was added to the Merriam-Webster Dictionary. Bitcoin and cryptocurrency technologies: Whether new cryptocurrency projects should have a large or small token supply is a hotly debated topic. American business magnate Warren Buffett thinks that cryptocurrency will come to a bad ending. These are useful for pump-and-dumpers, since they might get people excited to invest in a scam. A second problem is even worse: Just do the math; I bet just one 1 single bitcoin asic miner will achieve a higher hashrate than the largest botnet. This means that their addresses can be found, as well as customer reviews and open forums pertaining to the drugs being sold on the market, all without incriminating any form of user.
Business and economics portal Cryptography portal Free software portal Numismatics portal. First of all, being asic resistent is pretty much impossible. The implication is that the shill is paid to promote an illegitimate or scam product. All information on this website is for general informational purposes only, it is not intended to provide legal or financial advice. An average of 3 bitcoin ATMs were being installed per day in September He immediately switched to using a different cryptomining marketplace. Blockchain — a platform based on open, decentralized, and distributed processing and storage. Views Read Edit View history. So, miners still have something of value. Harnessing Bitcoin's Blockchain Technology. For example, it might not necessarily be a good idea to mine a cryptocurrency you think might be overvalued. There are plenty of articles, and office watercooler gatherings around the globe are buzzing with crypto-this and crypto-that. So while FUD is terrible for some hodlers, it protects a lot of long-term and risk-averse investors. Tether indicates that it is building a new core for its primary wallet in response to the attack in order to prevent the stolen coins from being used. With the private key, it is possible to write in the public ledger, effectively spending the associated cryptocurrency. Use this tool to help determine if content is stolen or not. In the American cryptographer David Chaum conceived an anonymous cryptographic electronic money called ecash. Mining requires more costs upfront buying mining equipment and less costs later on high exchange fees. Whatever algorithm can be executed on a GPU, can be executed more efficiently on a chip designed for that specific purpose. Anonymous Internet banking Bitcoin network Complementary currency Crypto-anarchism Cryptocurrency exchange Digital currency Double-spending Electronic money Initial coin offering Airdrop Virtual currency. Archived from the original on 19 January There is not an infinite choice of secure, proven hash algorithms. Also, more Proof-of-Work projects are moving towards PoS or hybrid consensus algorithms. I do not guarantee any results that may be obtained by using this information, and it should not be considered legal or financial advice. Bubble, Bubble, Fraud and Trouble". We recently published an article on this , and it is exactly what it sounds like: The amount of uninfected PC's is far greater.
Sumokoin Will Hard Fork to Remain Bitmain ASIC-Resistant
Resistant part comes from ability to change hashing algo and coins willing to do that, will be asic
Wallet Address In Genesis Mining Hash Line Cloud Mining. Some tokens built on Ethereum have billion-dollar market caps just in themselves. Since most darknet markets run through Torthey can be found with relative ease on public domains. By Marchhe was running seven computers, mining ether around the clock from his dorm room. Rekt — street slang to mean destroyed. Blockchains are secure by design and are an example of a distributed computing system with high Byzantine fault tolerance. By using this site, you agree to the Terms of Use and Privacy Policy. Miners regularly buy up the entire stock of new GPU's as soon as they are available, further driving prices up. This needs to be adopted by a large percentage
Coinpot Litecoin Miners Professional Cryptocurrency Miners miners and, given the community around the coin, would very likely be adopted straight away to deter any ASIC from gaining a large percentage of the mining power. Retrieved 24 February In some instances, it might be a good idea to trade
Does It Cost To Transfer Bitcoin Best Cloud Mining Ethereum mined cryptocurrency for another cryptocurrency or for fiat currency. And why is that good? The organization is dictated by rules written into the code and executed autonomously on the network. Archived from the original on 24 January Authors are also asked to include a personal bitcoin address in the first page of their papers. Whether new cryptocurrency projects should have a large or small token supply is a hotly debated topic.
A blockchain is a continuously growing list of records , called blocks , which are linked and secured using cryptography. One of the biggest things to consider is what consensus algorithm of the cryptocurrency you are interested in mining plans to use in the future. Based on the Bitcoin protocol, the blockchain database is shared by all nodes participating in a system. An ASIC can have , times more computational power than a standard desktop computer equipped with a few graphics cards. In , Wei Dai published a description of "b-money", an anonymous, distributed electronic cash system. Other miners described how they handled the massive amounts of heat—and what their significant others and roommates put up with. Baseless price speculation, shilling, repetitive posts et cetera are removed. Private keys are a bit like passwords, but they are often encrypted by a user-friendly password keys tend to be long. There are plenty of articles, and office watercooler gatherings around the globe are buzzing with crypto-this and crypto-that. Node — can be full or partial. Again, we've seen this before. Each time Mark mined enough ether to cover the cost, he bought a new graphics card, trading leftover currency into bitcoin for safekeeping. Once recorded, the data in any given block cannot be altered retroactively without the alteration of all subsequent blocks, which requires collusion of the network majority. So instead of having a few large mining operations that dedicate their business to crypto, you get a few large criminal operators controlling your hashrate. It can require a bit of subjectivity on the part of the miner. Archived from the original on 23 January Games, lotteries , online casinos and other online gambling sites that feature Cryptocurrency as either a method of payment or as the winnings paid have steadily increased as its popularity has grown and become widely accepted. In some instances, it might be a good idea to trade a mined cryptocurrency for another cryptocurrency or for fiat currency. Legal issues not dealing with governments have also arisen for cryptocurrencies.
 A guide to some other cryptocurrencies Archived at the Wayback Machine. Anonymous Distributed E-Cash from Bitcoin" pdf. To combat the scaling problem, some approaches perform considerable calculations or transfers outside the blockchain, only recording the essentials of results or portions Roger Ver Bitcoin Cash Litecoin Xvg results on the blockchain for posterity. Retrieved 4 April Can this Storm Be Weathered? Retrieved 22 October Im seeing a small army of redditors pumping asic resistant coins lately, claiming that makes it more decentralised. Someone will do it. Archived from the original on 12 January The coins may ultimately be intended to be used as a medium of payment on a platform or serve some other purpose such as identity verification within an ecosystem. We recently published an article on thisand it is How To Buy Cryptocurrency With Cash Crypto Cheatsheet what it sounds like: Trading or mining any form of cryptocurrency is very high risk, so never invest money you Can You Buy On Poloniex With Credit Card Crypto And Alt Coin Price Ticker afford to lose - you should be prepared to sustain a total loss of all invested money. April 6th, What is Monero? The price may meander along at for three days, but then it jumps to in an hour, then to the. However, it also makes it more difficult for entrepreneurs with a lot of money to be able to mine at scale. This needs to be adopted by a large Withdraw From Hashflare To Coinbase Types Of Altcoins of miners and, given the community around the coin, would very likely be adopted straight away to deter any ASIC from gaining a large percentage of the mining power. Time to dispel that myth. Archived from the original on 26 October Retrieved 4 December It used SHAa cryptographic hash function, as its proof-of-work scheme. Rekt — street slang to mean destroyed. Transaction fees for cryptocurrency depend Bitcoin 24 Hour Growth Can Novice Mine Litecoin on the supply of network capacity at the time, versus the demand from the currency holder for a faster transaction. Requires comment karma and 1-month account age. GBL, a Chinese bitcoin trading platform, suddenly shut down on October 26, An average of 3 bitcoin ATMs were being installed per day in September
A guide to some other cryptocurrencies Archived at the Wayback Machine. Anonymous Distributed E-Cash from Bitcoin" pdf. To combat the scaling problem, some approaches perform considerable calculations or transfers outside the blockchain, only recording the essentials of results or portions Roger Ver Bitcoin Cash Litecoin Xvg results on the blockchain for posterity. Retrieved 4 April Can this Storm Be Weathered? Retrieved 22 October Im seeing a small army of redditors pumping asic resistant coins lately, claiming that makes it more decentralised. Someone will do it. Archived from the original on 12 January The coins may ultimately be intended to be used as a medium of payment on a platform or serve some other purpose such as identity verification within an ecosystem. We recently published an article on thisand it is How To Buy Cryptocurrency With Cash Crypto Cheatsheet what it sounds like: Trading or mining any form of cryptocurrency is very high risk, so never invest money you Can You Buy On Poloniex With Credit Card Crypto And Alt Coin Price Ticker afford to lose - you should be prepared to sustain a total loss of all invested money. April 6th, What is Monero? The price may meander along at for three days, but then it jumps to in an hour, then to the. However, it also makes it more difficult for entrepreneurs with a lot of money to be able to mine at scale. This needs to be adopted by a large Withdraw From Hashflare To Coinbase Types Of Altcoins of miners and, given the community around the coin, would very likely be adopted straight away to deter any ASIC from gaining a large percentage of the mining power. Time to dispel that myth. Archived from the original on 26 October Retrieved 4 December It used SHAa cryptographic hash function, as its proof-of-work scheme. Rekt — street slang to mean destroyed. Transaction fees for cryptocurrency depend Bitcoin 24 Hour Growth Can Novice Mine Litecoin on the supply of network capacity at the time, versus the demand from the currency holder for a faster transaction. Requires comment karma and 1-month account age. GBL, a Chinese bitcoin trading platform, suddenly shut down on October 26, An average of 3 bitcoin ATMs were being installed per day in September
